Blog

My day usually starts with a morning walk around my city’s seaside, it energizes my mind and body so I can prepare for the day’s tasks...

As businesses increasingly rely on cloud-based applications, managing access efficiently becomes a top priority...

In today's fast-paced, cloud-driven world, managing and monitoring your applications is essential...

DevOps professionals rely on a wide array of tools to streamline workflows, manage infrastructure, and automate processes...

In the fast-paced world of DevOps, security and efficiency are top priorities, especially when it comes to maintaining private networks....

For businesses running on Amazon Web Services (AWS), it’s easy to get caught off guard by escalating cloud costs...

In today’s cloud-driven world, businesses face a crucial decision: should they opt for managed cloud services or go the self-managed route?...

Becoming a professional in the IT industry is an exciting journey filled with learning, curiosity, and problem-solving...

Entering the world of DevOps can seem daunting, especially with the vast number of skills, tools, and concepts involved. But by following a structured approach, anyone with a passion for technology can successfully become a DevOps professional...

When designing the data layer of an application, one of the key decisions you’ll face is choosing the right type of database....

In recent years, the conversation around software development and infrastructure management has shifted from DevOps to a newer term: Platform Engineering....

In the world of DevOps, the debate between monolithic architectures and microservices has become a topic of significant debate....

When it comes to cloud infrastructure, two of the most frequently used Amazon Web Services (AWS), are Relational Database Service (RDS) and Elastic Compute Cloud (EC2)....
Generative AI is revolutionizing how businesses leverage artificial intelligence for complex tasks like text generation, problem-solving, and even code development....

Kubernetes, often hailed as a revolutionary technology for container orchestration, is increasingly becoming the go-to solution for organizations of all sizes....
In today's data-driven world, organizations are constantly looking for ways to manage and analyze vast amounts of data efficiently and affordably....

Security in today’s digital landscape is a critical priority for businesses, especially those running APIs and other backend services that require stringent access control....

Deploying applications in the cloud has never been easier, thanks to the wide array of tools and services available on Amazon Web Services (AWS)....
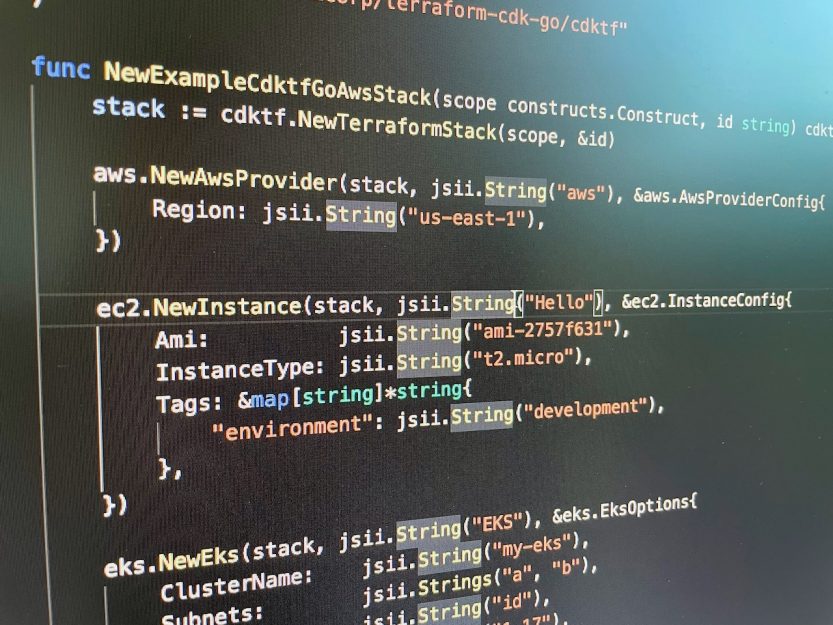
If you want to provision infrastructure using familiar programming languages rather than using the HashiCorp Configuration Language (HCL), you can now do so using the Cloud Development Kit for Terraform (CDKTF)...

Another amazing team member who provides IN4IT with unparalleled service is Pablo Serrano Jabonero, our resident Site Reliability Engineer who has been with us for nearly three years...

Here at IN4IT, we believe in being remote-first, since that not only allows us to attract the best talent possible but also puts us in the perfect position to service our worldwide clientele with our AWS consulting services....

Here at IN4IT, we believe in being remote-first, since that not only allows us to attract the best talent possible but also puts us in the perfect position to service our worldwide clientele with our AWS consulting services....

Alessandro Marino is one of the many wonderful team members who have given their best to the job and have ensured the delivery of high-quality work and a diligent work ethic...

Why Your Company Should Adopt a Container Strategy to Reduce Cost and Improve Developer Productivity...

We are proud to announce that IN4IT gained AWS advanced consulting partner status. We want to thank all customers, employees, and AWS for helping us achieve the coveted standing. We are a member of this group of partners, along with a list of different incredible companies....

SweepBright transforms each step of the real estate transaction process into a fully digital journey. Its rich stack of features possible by an open architecture, empowers real estate agencies of any kind to become far more efficient and deliver exceptional customer experiences...

This is the 3rd part of IN4IT’s “Kubernetes Security blog series”. In this blog we are going to cover what Pod Security Policies are. How can they help you secure your Kubernetes cluster and how to implement them....

Once you start deploying applications to Kubernetes, you quickly realize Secrets Management takes a lot of time to get right. The Kubernetes Secret and ConfigMap objects don’t yet have all the features you’d expect to properly setup Secrets Management. Until Kubernetes has these capabilities built-in, you’ll have to come up with your own mechanism to deal with secrets....

First of all, you need to think about what kind of network traffic you want to filter. The easiest way filtering traffic is on Layer 3 and 4, which is at the IP address and port level. If you’d like to filter on http/https hostname, then you’ll need Layer 7 filtering, which is currently not supported by Kubernetes Network Policies. For that, you would need a separate proxy server within your cluster....

Extremely proud to show you how we helped our FinTech costumer Cake to deliver a resilient and secure banking platform using Amazon Web Services....

Techradar reported in early 2020 that Amazon Web Services now has 175 products. Between the start of SQS (November 2004) and August 2020, there are more than 7500 announcements made on "What’s new at AWS"....
Companies often fall into the trap of building standardized infrastructure themselves, then offer it to their teams to run their workloads on...
When Amazon started rewriting its closed source software for networking devices, they started with a warning that it'll get worse first before it’ll get better...

Every time you're reading about yet another unprotected S3 bucket that has leaked, you’re probably wondering how is it possible to let this happen...
AWS Users and Roles can have their permissions limited by a Permission Boundary. The effective permissions are at the intersection of the user or role policy and the permission boundary...

Cake brings together all your existing bank accounts and transactions. The app analyses your financial data and habits, to make your life better...
Employees typically get a laptop or workstation to do their work. Contractors use their own laptops or workstations in most cases. This brings all kinds of challenges on how to manage and secure these...

JWTs (JSON Web Tokens) provide an easy and scalable way to perform user access control. JWTs are often used in microservices...
Data partitioning helps to speed up your Amazon Athena queries, and also reduces your cost, as you need to query less data...

Learn how we ingest, process, and visualize data at a price point you never thought was possible....

IN4IT offers 24/7 support contracts to its customers. It’s very important for us that our customers can easily and reliably reach IN4IT when they need assistance...

IN4IT has been selected to be the go-to cloud partner for a financial data analytics firm called Cake...

Even 5-10 year old java applications can be containerized and migrated to the cloud...
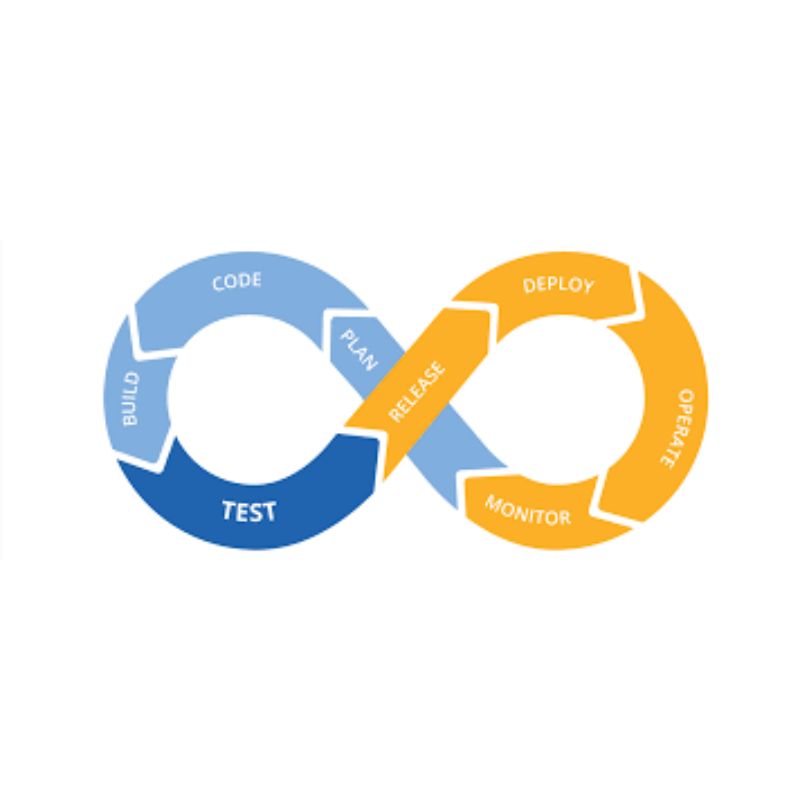
The prerequisite of being able to deploy through a fully automated pipeline is to have cloud native applications...

My latest course is all about scaling applications on-premise and in the cloud. I just a few paragraphs I'll explain why you would want to make your application scalable and how you would do it...

My latest course is all about scaling applications on-premise and in the cloud. I just a few paragraphs I'll explain why you would want to make your application scalable and how you would do it...

Due to the nature of microservices the system is composed out of collaborating services, for each of these services you can, but don't need to, use a different technology...

AWS ReInvent Executive Summary. AWS has more than 1 million active customers (2015)...

The traditional monolithic application architecture is easy to develop, test, and deploy. Unfortunately those applications tend to become large, complex, and as a team it's difficult to work together on the app...

Today, software is often delivered as a service. 12factor is a methodology for building software-as-a-service applications. By using this methodology, you ensure best practices and lots of business benefits that come with it...

Today we want to focus on the app, not on the operations involved by running a zero-downtime, scalable, resilient (web) application...

NASA gathered approximately 1.73 gigabytes of data before you are able to reach the end of this sentence...

The big operational cost of applications is maintenance....

Implementing DevOps starts with optimizing your existing Software Development LifeCycle to bring Dev and Ops closer together...

The big operational cost of applications is maintenance....

Every Cloud provider wants you to sign up for their services. To do that, they will offer you some free services....

