Employees typically get a laptop or workstation to do their work. Contractors use their own laptops or workstations in most cases. This brings all kinds of challenges on how to manage and secure these. In small and medium companies there is often no time or resources to ensure the laptop is and stays secure. When employees start working with sensitive data, that sensitive data will frequently end up stored on the laptop. Security controls to prevent a data breach are often lacking and implementing desktop controls can be expensive, time-consuming, and if badly executed, can impact the performance of the employee working on the device.
A Unified Virtual Desktop for employees is a solution that can mitigate these risks. Amazon has a product called WorkSpaces, which is a managed, secure Desktop-as-a-Service (DaaS) solution. We implement this for customers who need a reliable, secure, unified desktop solution for their employees.
Benefits
Adopting workspaces brings some immediate benefits:
- Workspaces launch in a VPC, so all data and local data transfer will be kept within your own private network
- There’s no data stored on the employee’s laptop (willingly or unwillingly)
- AWS Credentials issued can be locked down to the VPC, avoiding the credentials to be used outside the Workspaces
- A lower attack vector, because company data and information is shielded within the virtual environment instead of on the physical machine
- Network controls can be implemented easily to reduce confidential data to be leaked outside own network
- Copy-paste from workspace to the physical desktop can be prohibited to ensure data is kept within virtual environment
- Unified working environment with the same software and policies for every employee
Example Architecture
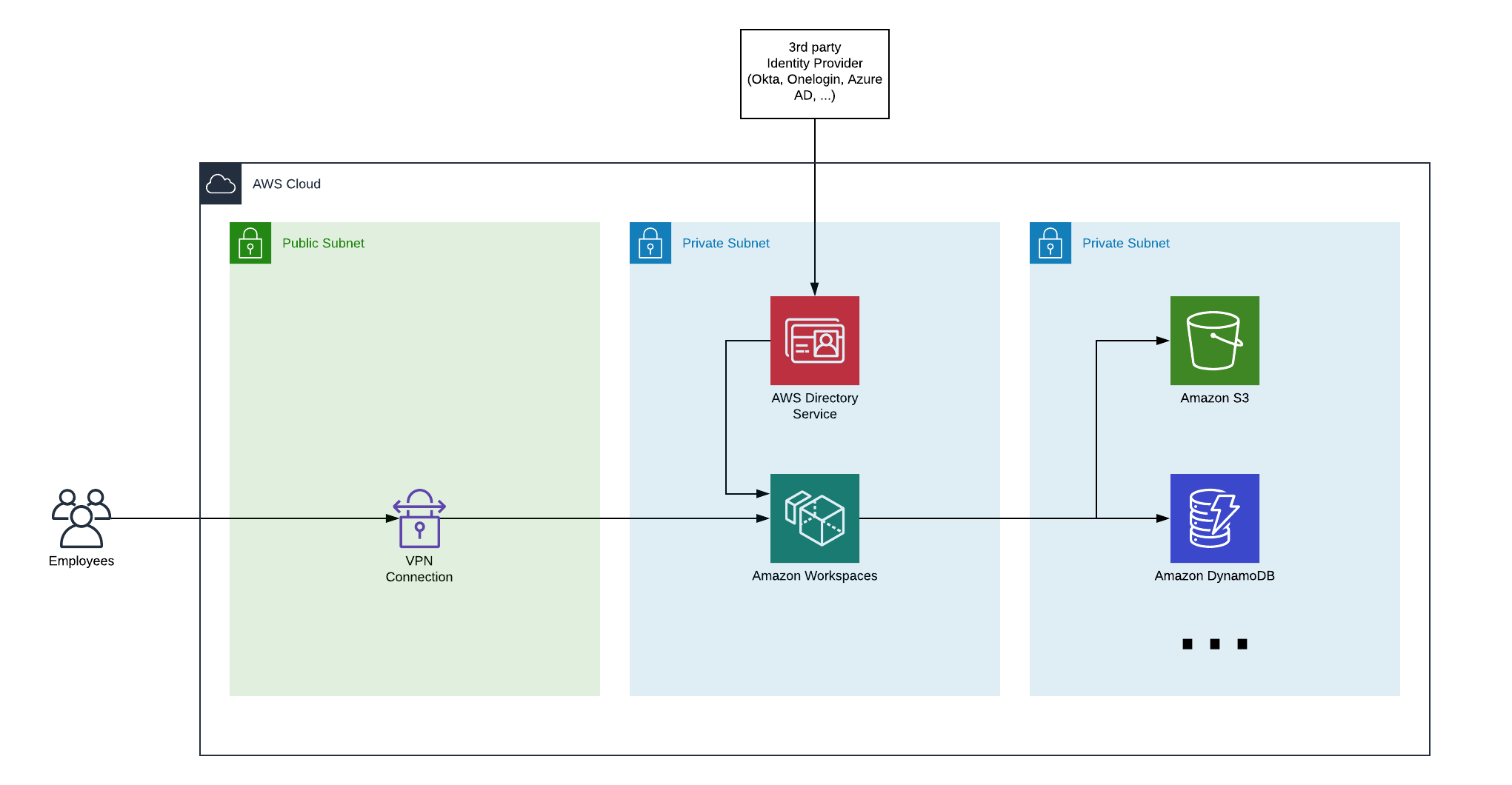
Amazon Workspaces uses AWS Directory Services for authentication. If you choose to go with Microsoft AD as a managed Directory Service, you can still integrate this with popular identity providers (like Onelogin, or Okta), allowing you to use the same login and password policies as you have defined in your identity provider.
We typically run workspaces in a private subnet. To reach your private subnet, you can use a VPN Connection (using AWS’s VPN service, or standalone software). When an employee wants to use workspaces, it’ll first need to initiate a VPN connection, then it can use a Workspace client to start the workspace. Once in the Workspace, the employee can use the desktop (Windows or Linux) and access other AWS services that are typically available only through private subnets within the VPC. To make these AWS services available within your VPC, you can use AWS VPC Endpoint interfaces and gateways.
Our Security Enhancements
We always try to deploy our solutions with security in mind. The following is a list of extra security enhancements we enabled:
- Disable copy-paste in the Workspaces (copy-paste to the virtual workspace is allowed, other direction not)
- Workspaces storage encrypted with KMS key
- 2FA for VPN (2FA can also be enabled on the workspace through AD)
- Third party provider policies are applied on the AD automatically through syncing mechanisms. Login & Passwords are also synced automatically
- Workspace traffic is tunneled over the VPN.
- IP limits on the Workspace are in effect to only allow VPN traffic
- IAM Policies used within the Workspace have Permission Boundaries to restrict the usage. The credentials are only allowed to be used within the VPC (within the workspace) and not on any external machine (this prevents users from copy-pasting credentials and using them on their machines)